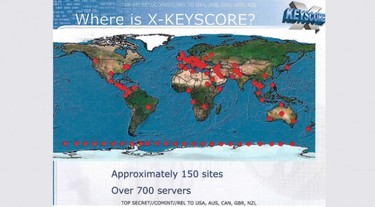
 From Extremetech via the Guardian newspaper: From Extremetech: "If you were shocked by the NSA’s Prism program, hold onto your hat: The NSA also operates another system, called XKeyscore, which gives the US intelligence community (and probably most of the US’s Western allies) full access to your email, IMs, browsing history, and social media activity. To view almost everything that you do online, an NSA analyst simply has to enter your email or IP address into XKeyscore. No formal authorization or warrant is required; the analyst just has to type in a “justification” and press Enter. To provide such functionality, the NSA collects, in its own words, “nearly everything a typical user does on the internet.” Perhaps most importantly, though, it appears that HTTPS and SSL might not protect your communications from being snooped on by the NSA." Here is a link to the NSA slideshow discussing Xkeyscore While this system may not actively seek out the identity of an individual, according to slide 12 it does index "every email address seen in a session", "every file seen in a session", "every phone number seen in a session", and "the webmail and chat activity to include username, buddylist, machine specific cookies", etc. Anyone who believes that very specific information could not be gathered on an individual just from the metadata in such communications is deceiving themselves, and this program seems to go far beyond gathering just metadata. Worse (or better, I suppose, if you are a security analyst and not a private citizen concerned about your own privacy), slide 17 highlights some of the uses for XKeyscore, such as: "Show me all the VPN startups in country X, and give me the data so I can decrypt and discover the users" and "show me all the exploitable machines in country x". Now, the first of those sounds like this program can identify secure traffic on the Internet, and then help the user decrypt it, which makes me wonder just how secure our standard "best practice" Internet security is. The second is arguably more serious. It implies that the XKeyscore program can identify all computers in a target area that can be attacked by a specific bit of code (virus, malware, keylogger, etc.) and more than likely automatically take care of distributing that exploit. Perhaps not a terrible thing if good people are only using this in a very targeted way against very bad people, but if the "good guys" can do it, then other people can probably figure out how to do it too, if they haven't already. Regardless of whether you believe Edward Snowden did the right thing or the wrong thing, and regardless of whether or not you believe the US Government (and whatever other governments have access to similar programs) will only use these kinds of "powers" responsibly and for the greater good, the very existence of such capabilities should give us all cause for concern. At best, programs like Xkeyscore and PRISM (and who knows how many other similar but differently-named projects exist out there... we all watched or read the Jason Bourne stories, right?) could inadvertently provide governments with information that they should have no rights to. At worst... Well, I'd rather not dwell on a worst case scenario here. This seems like the kind of issue that should have Civil Rights and Privacy Rights advocates joining forces, demanding more information and at least requiring some real and legitimate oversight in hopes of ensuring these types of information-gathering programs are used only in the way their designers claim they are intended. Of course, that would require something to happen in Congress. Maybe the NSA has designed a program that prevents them from accomplishing any meaningful work.
0 Comments
Leave a Reply. |
Bret FunkCompTIA A+ Certified Technician Archives
July 2016
Categories
All
|

 RSS Feed
RSS Feed