|
A new family of Android malware codenamed Hummer has been discovered that installs malware and unwanted apps on affected devices. This malware infects the device in such a way that not even a factory reset can remove it; the only known guaranteed fix is to re-flash the phone with a clean OS image.
If you device is showing abnormal pop-ups and has apps installing that you do not remember, you may be infected. Before download apps to your devices, be sure that they are coming from a reliable source.
1 Comment
A three-year old bug was identified in the Linux kernel which allows drivers to cache encryption keys and authentication codes, providing a path by which even secured devices could be accessed. This bug affects Android version 4.4 (Kitkat) and later, rendering nearly 70% of all Android devices vulnerable. The good news is that there is no known reported malware that has taken advantage of this exploit, so even though the security threat remains to be patched, it may have been caught before it posed a significant risk to users.
We're all aware (even if we don't always like it) that the big data companies like Google, Apple, Microsoft, and Amazon are monitoring our online habits and hoping to capitalize on them... But we'd all be naive to think that other corporations aren't interested in trying to monetize our actions...
When you are watching your TV, are you sure it isn't watching back? Vizio (and other smartTVs to a lesser extent) have been caught monitoring and reporting viewing habits, with the intent to sell that data to advertisers. Vizio has gone so far as to put into its terms of service that it “may combine this information with other information about devices associated with that IP address.” In other words, your “smart” TV is smart enough to hunt for other devices that connect to the local network and to sell that information." There are laws in place that control what cable and video companies can do with the data users stream, but Vizio's legal team claims there business manufactures products and is not subject to those laws. Vizio's now the only one... XBox One was under fire before its release for its intended requirements to be always on (even when off) and to have a steady Internet connection to function, with the supposed intention of monitoring what went on in and around the device for targeted advertising (thanks to the built in camera and microphone). Verizon is unashamedly selling information to advertisers. And the list goes on and on. It used to be that the trade-off for getting something for free on the Internet was that our information was going to be sold. Now it seems like the trend is to steal and sell our information regardless of whether or not we have paid for something. A vulnerability was discovered in iOS 8.1.2 that could allow fake login prompts to be sent to users, possibly compromising sensitive account information.
This vulnerability was reported in January but remains unpatched even in the developer previews of iOS 8.4 and 9.0 Beta. Identifying a fake login prompt is not impossible. With a genuine login prompt in iOS users must either press OK or Cancel to proceed past the prompt. A fake login prompt can be bypassed with the Home button. We've talked about encryption viruses before, but this techrepublic article goes into more depth about one of the latest variants of encryption virus, and offers some suggestions about how to protect yourself.
The best chance for recovery from an encryption virus is a active backup with multiple revisions. InfinIT's monitored offsite backup options cost as little as $.75/GB, and for those with large amounts of static data (pictures, music, videos), we can leverage the power of our Cloud Sync software's backup feature to provide storage space of up to 100GB for as little as $10/month. The best method of protection from encryption viruses is user education. Most of these viruses install themselves because of direct interaction from users. Maintain good security on your computers and make sure to follow links wisely! 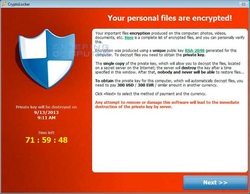 Cryptolocker is a form of ransomware that encrypts data on the infected computer, rendering the files unreadable without the decryption key. Affected users are prevented with a screen with a countdown timer informing them that unless they pay the ransom for their data in a certain number of hours, the decryption key will be deleted. Initial Infection: The initial infection is usually received via an email attachment or "drive-by" download on an infected website. Once installed, the malware contacts its "command and control" center for instructions, which provides the malware with the encryption key and its list of targeted file types. Repair: While the infection itself can be removed without much difficulty by qualified IT professionals, without the decryption key, restoration of the encrypted data is impossible. Without paying the ransom, there is no way to obtain the decryption key, and due to the large key size, brute force decryption techniques are generally considered impossible. Early versions of Cryptolocker could be circumvented with a good system restore point, but later versions also encrypt or delete the pre-existing restore points, rendering that repair option useless. Aside from paying the ransom, the only reliable way to recover encrypted data is from a good backup of the user files. Prevention and Remediation: While there are no guarantees in regards to malware, having a reliable and up-to-date antivirus program running on a computer can help prevent the initial infection by Cryptolocker malware. Similarly, utilizing a high-quality firewall or network monitoring service that prevents the malware from contacting its command and control center can stop an infected machine from receiving its encryption key and instructions. Finally, if an infection with Cryptolocker does occur, having a reliable backup of critical information, or (even better) a disk image to restore from is the only way to recover data lost to encryption. InfinIT Technology Group offers Managed Antivirus ($3/device/month), 24/7 Remote Monitoring ($3/device/month), and Web Protection & Content Filtering Services ($3/device per month), or bundle all three services for $7/device/month. InfinIT can also help design a local backup strategy, make a baseline disk image, or set up an offsite backup for customers interested in protecting their most important data. If you are worried about the Heartbleed security flaw but don't know what passwords you need to change, mashable has provided a short list of major websites, and whether or not they were affected by the flaw. If you have any doubts or concerns about a site not on this list, better safe than sorry: change your login password to something new and secure.
It turns out it doesn't matter, since 95% of the top 200 free iOS and Android apps have at least one risky behavior. But iOS apps were 8% more likely overall to exhibit risky behavior.
Over the last few weeks, we've had several customer bring in virus-infected computers, and all were certain that the only place they had gone on the Internet was to their favorite news sites.
Lo and behold, a week or so later and reports are coming out of a new type of malware that seeks to infect machines by posing as news sites, often originating as a fake link or phishing attempt. The worst of this new type of malware is dubbed Careto, which is able to collect a plethora of sensitive information from an infected system, such as keystrokes, WiFi traffic data, and file operations. It can also capture screenshots and Skype conversations, as well as intercept your email. And Mac Users, don't let your guard down. Careto has Along with WIndows XP, Microsoft is ending support for Office 2003 at the beginning of April. While the programs themselves will continue to function, the lack of security updates means that any exploits found in the software will go unpatched and represent an ongoing threat to your network.
Now is a good time to look into upgrading your old versions of Office 2003. The best thing for you to upgrade to will depend on your individual needs and the number of machines you need to upgrade, but there are more options that just Microsoft ones. If you need help choosing an upgrade path, contact InfinIT Technology Group. |
Bret FunkCompTIA A+ Certified Technician Archives
July 2016
Categories
All
|

 RSS Feed
RSS Feed